Software Testing Methods
Black-Box testing
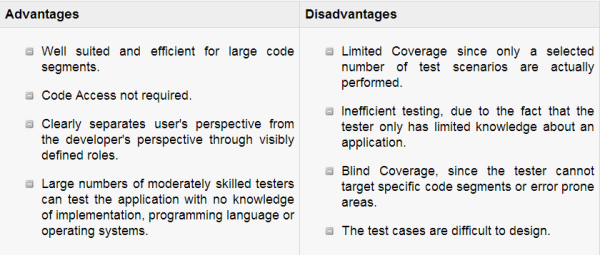
Black-box testing is a method of software testing that examines the functionality of an application based on the specifications. It is also known as Specifications based testing. Independent Testing Team usually performs this type of testing during the software testing life cycle.
This method of test can be applied to each and every level of software testing such as unit, integration, system and acceptance testing. The tester is oblivious to the system architecture and does not have access to the source code. Typically, when performing a black box test, a tester will interact with the system’s user interface by providing inputs and examining outputs without knowing how and where the inputs are worked upon.
White-Box testing
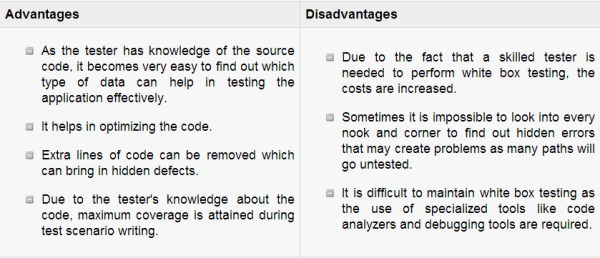
White box testing is a testing technique, that examines the program structure and derives test data from the program logic/code. The other names of glass box testing are clear box testing, open box testing, logic driven testing or path driven testing or structural testing.
White box testing is the detailed investigation of internal logic and structure of the code. White box testing is also called glass testing or open box testing. In order to perform white box testing on an application, the tester needs to possess knowledge of the internal working of the code.
The tester needs to have a look inside the source code and find out which unit/chunk of the code is behaving inappropriately.
Grey-Box testing
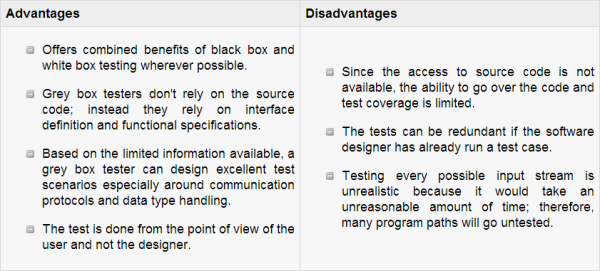
Grey Box testing is testing technique performed with limited information about the internal functionality of the system. Grey Box testers have access to the detailed design documents along with information about requirements.
Grey Box tests are generated based on the state-based models, UML Diagrams or architecture diagrams of the target system. In software testing, the term the more you know the better carries a lot of weight when testing an application.
Mastering the domain of a system always gives the tester an edge over someone with limited domain knowledge. Unlike black box testing, where the tester only tests the application’s user interface, in grey box testing, the tester has access to design documents and the database. Having this knowledge, the tester is able to better prepare test data and test scenarios when making the test plan.
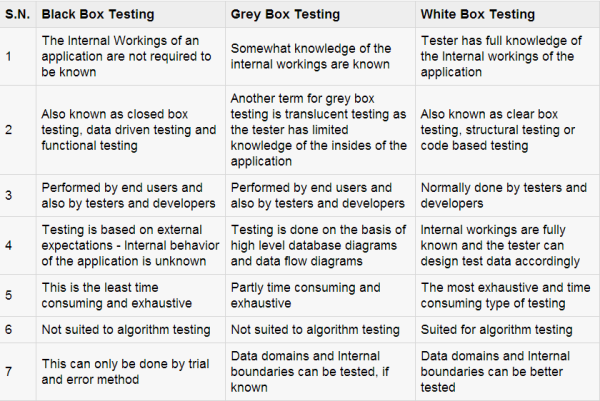
Black-Box testing vs Grey-Box testing vs White-Box testing
Software Testing
Testing is the process of evaluating a system or its component(s) with the intent to find that whether it satisfies the specified requirements or not. Testing is executing a system in order to identify any gaps, errors or missing requirements in contrary to the actual desire or requirements.
Software testing is the process of evaluation a software item to detect differences between given input and expected output. Also to assess the feature of A software item. Testing assesses the quality of the product. Software testing is a process that should be done during the development process. In other words software testing is a verification and validation process.
In the software testing, there are two basic of testing or testing methods.
- Black-Box testing
- White-Box testing
Black box testing is often used for validation and white box testing is often used for verification.
Black box testing is a testing technique that ignores the internal mechanism of the system and focuses on the output generated against any input and execution of the system. It is also called functional testing.
White box testing is a testing technique that takes into account the internal mechanism of a system. It is also called structural testing and glass box testing.
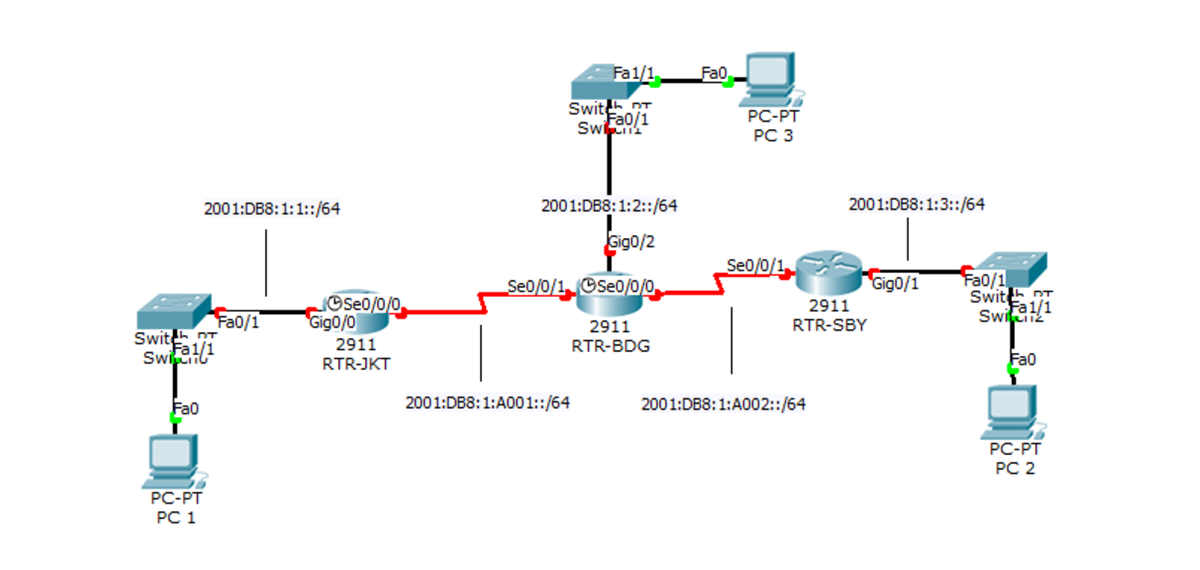
Implementing IPv6 using RIPng
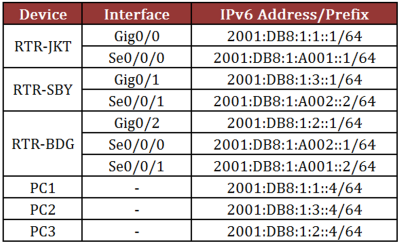
RIPng is designed to allow routers to exchange information to compute routes in IPv6-enabled network. RIPng relies on certain information about each of the networks, mainly the metric. RIPng metric is a value between 1 and 15, inclusive. The maximum path limit is 15, after which the network is considered unreachable. RIPng supports multiple IPv6 addresses on each interface.
RIPng is similar to RIPv2, the biggest difference is the RIPv2 uses IPv4 while RIPng uses IPv6. The routing command is also different between RIPv2 and RIPng.
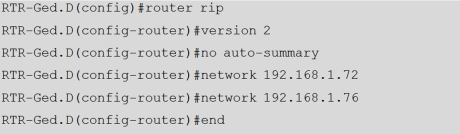 Picture 1. RIPv2 Configuration
Picture 1. RIPv2 Configuration
The image above is a routing RIPv2 configuration using IPv4. Using command “router rip” and then input the network address, we create a RIPv2 configuration.
There are clear differences between RIPng configuration and RIPv2 configuration. Despite from the uses of IP address version, there also a differences in their configuration command.
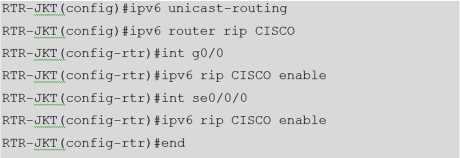 Picture 2. RIPng configuration
Picture 2. RIPng configuration
As we can see, in RIPng configuration we don’t need to use “router rip” and then “version x”. We just have to enter the “process name” in each interface to enable the RIPng routing. In IPv6 there’s 3 addressing modes; Unicast, Multicast, and Anycast. In this section we use Unicast.
In unicast mode of addressing, an IPv6 interface (host) is uniquely identified in a network segment. The IPv6 packet contains both source and destination IP addresses. A host interface is equipped with an IP address which is unique in that network segment. A network switch or router when receives a unicast IP packet, destined to single host, sends out to one of its outgoing interface which connects to that particular host.
[LAB]
First, make the topology in your packet tracer or you can download the file include Cisco Packet Tracer installer, here the download link.
Download – [LAB]Configuring RIPng CISCO + Cisco Packet Tracer 6.01 for Windows
Second, assign the IP address in each interface based on the routing table.
There’s a different command in assigning IPv4 and IPv6. After enter the interface, type “ipv6 address xxxx:xxxx:xxxx::x/xx” to assign IPv6 in the interface.
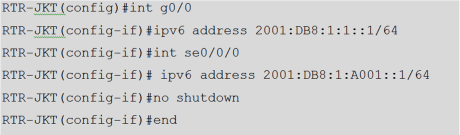 Picture 5. IPv6 address command
Picture 5. IPv6 address command
Afterward, we configure the routing RIPng in the router. One thing that must be remember, RIPng has a “process name”. This process name will be assign in every interface in the router that we want to route. And don’t forget to enter the “ipv6 unicast-routing” in every router, if you don’t do this the routing won’t be work.
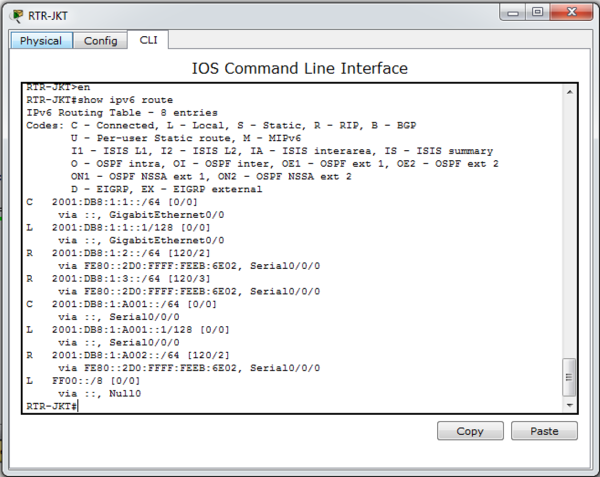
And the last, enter the “show ipv6 route” in any router to check if RIPng is already in routing table or not.
IPv6, a new generation of Internet Protocol
Internet Protocol version 6 (IPv6) is the latest revision of the Internet Protocol (IP) and the first version of the protocol to be widely deployed. IPv6 was developed by the Internet Engineering Task Force (IETF) to deal with the long-anticipated problem of IPv4 address exhaustion.
“What is the advantage of IPv6? I think using IPv4 is enough for me. As long as I can connect to the internet.”
Yes, you still can connect to the internet using IPv4. But, if you know almost 3/4 from all people in the world is using internet right now. Let’s say human population in the world right now is around 7 billion. So if we calculate it, there’s around 5.25 billion people using internet! Can you imagine that?!
The limit address of IPv4 is 4294967296 (232) addresses. Maybe it’s still have enough IP address, if every people in this world only have one PC/Laptop to connect to the internet. And when we talk about a company, we don’t talk about one PC or one Laptop. They use a hundred of PC to work everyday.
If we talk about features, IPv6 offers the following features:
- Larger Address Space:
In contrast to IPv4, IPv6 uses 4 times more bits to address a device on the Internet. This much of extra bits can provide approximately 3.4×1038 different combinations of addresses. This address can accumulate the aggressive requirement of address allotment for almost everything in this world. According to an estimate, 1564 addresses can be allocated to every square meter of this earth.
- Simplified Header:
IPv6’s header has been simplified by moving all unnecessary information and options (which are present in IPv4 header) to the end of the IPv6 header. IPv6 header is only twice as bigger than IPv4 providing the fact the IPv6 address is four times longer.
- End-to-end Connectivity:
Every system now has unique IP address and can traverse through the internet without using NAT or other translating components. After IPv6 is fully implemented, every host can directly reach other host on the Internet, with some limitations involved like Firewall, Organization’s policies, etc.
- Auto-configuration:
IPv6 supports both stateful and stateless auto configuration mode of its host devices. This way absence of a DHCP server does not put halt on inter segment communication.
- Faster Forwarding/Routing:
Simplified header puts all unnecessary information at the end of the header. All information in first part of the header are adequate for a Router to take routing decision thus making routing decision as quickly as looking at the mandatory header.
- IPSec:
Initially it was decided for IPv6 to must have IPSec security, making it more secure than IPv4. This feature has now been made optional.
- No Broadcast:
Though Ethernet/Token Ring are considered as broadcast network because they support Broadcasting, IPv6 does not have any Broadcast support anymore left with it. It uses multicast to communicate with multiple hosts.
- Anycast Support:
This is another characteristic of IPv6. IPv6 has introduced Anycast mode of packet routing. In this mode, multiple interfaces over the Internet are assigned same Anycast IP address. Routers, while routing, sends the packet to the nearest destination.
- Mobility:
IPv6 was designed keeping mobility feature in mind. This feature enables hosts (such as mobile phone) to roam around in different geographical area and remain connected with same IP address. IPv6 mobility feature takes advantage of auto IP configuration and Extension headers.
- Enhanced Priority support:
Where IPv4 used 6 bits DSCP (Differential Service Code Point) and 2 bits ECN (Explicit Congestion Notification) to provide Quality of Service but it could only be used if the end-to-end devices support it, that is, the source and destination device and underlying network must support it.
In IPv6, Traffic class and Flow label are used to tell underlying routers how to efficiently process the packet and route it.
- Smooth Transition:
Large IP address scheme in IPv6 enables to allocate devices with globally unique IP addresses. This assures that mechanism to save IP addresses such as NAT is not required. So devices can send/receive data between each other, for example VoIP and/or any streaming media can be used much efficiently.
Other fact is, the header is less loaded so routers can make forwarding decision and forward them as quickly as they arrive.
- Extensibility:
One of the major advantage of IPv6 header is that it is extensible to add more information in the option part. IPv4 provides only 40-bytes for options whereas options in IPv6 can be as much as the size of IPv6 packet itself.
So far, IPv4 has proven itself as a robust routable addressing protocol and has served human being for decades on its best-effort-delivery mechanism. It was designed in early 80’s and did not get any major change afterward. At the time of its birth, Internet was limited only to a few Universities for their research and to Department of Defense. IPv4 is 32 bits long which offers around 4,294,967,296 (232) addresses. This address space was considered more than enough that time. Soon or later we will running out of IP addresses. That’s why we must switch from IPv4 to IPv6.
Pidato Wisudawan Terbaik, Memukau tetapi Sekaligus “Menakutkan”
Renungan …
Setiap acara wisuda di kampus ITB selalu ada pidato sambutan dari salah seorang wisudawan. Biasanya yang terpilih memberikan pidato sambutan adalah pribadi yang unik, tetapi tidak selalu yang mempunyai IPK terbaik. Sepanjang yang saya pernah ikuti, isi pidatonya kebanyakan tidak terlalu istimewa, paling-paling isinya kenangan memorabilia selama menimba ilmu di kampus ITB, kehidupan mahasiswa selama kuliah, pesan-pesan, dan ucapan terima kasih kepada dosen dan teman-teman civitas academica.
Namun, yang saya tulis dalam posting-an ini bukan pidato wisudawan ITB, tetapi wisudawan SMA di Amerika. Beberapa hari yang lalu saya menerima kiriman surel dari teman di milis dosen yang isinya cuplikan pidato Erica Goldson (siswi SMA) pada acara wisuda di Coxsackie-Athens High School, New York, tahun 2010. Erica Goldson adalah wisudawan yang lulus dengan nilai terbaik pada tahun itu. Isi pidatonya sangat menarik dan menurut saya sangat memukau. Namun, setelah saya membacanya, ada rasa keprihatinan yang muncul (nanti saya jelaskan).Cuplikan…
View original post 2,517 more words
Today’s #quote
虎穴に入らずんば虎子を得ず。 (Koketsu ni irazunba koji wo ezu)
Literally: If you do not enter the tiger’s cave, you will not catch its cub.
This means: Nothing ventured, nothing gained. / You can’t do anything without risking something.
The 10 Fastest Super-Computer in the World
#1: Tianhe-2, National University of Defense Technology in China
The followup to Tianhe-1A, the new world’s #1 broke the speed record with performance of 33.86 petaflops. Tianhe-2 uses Ivy Bridge-based Intel Xeons and Intel Xeon Phi for a total of 3.12 million cores. The computer uses 17,808 kilowatts of power and can theoretically hit speeds of up to 54.9 petaflops.
#2: Titan, Oak Ridge National Laboratory
Titan was #1 last November with a speed of 17.6 petaflops. The system uses AMD-based Cray CPUs and Nvidia GPUs in its 560,640 cores. Rated the third most energy efficient supercomputer last November, Titan uses 8,209 kilowatts of power.
#3: Sequoia, Lawrence Livermore National Laboratory
The world’s #1 supercomputer in June 2012, Sequoia is used by the National Nuclear Security Administration to conduct simulations aimed at extending the lifespan of nuclear weapons. The Blue Gene/Q system has nearly 1.6 million cores and hits speeds of 17.2 petaflops.
#4: K computer, RIKEN Advanced Institute for Computational Science in Japan
Ranked #1 in the world in 2011, the K computer was made by Fujitsu. Delivering 10.5 petaflops with 705,024 Sparc cores, the K computer uses a six-dimensional torus interconnect called Tofu.
#5: Mira, Department of Energy’s Argonne National Laboratory
This Blue Gene/Q system uses 786,432 cores to hit 8.6 petaflops. When it hits full production in 2014 Mira will offer more than 5 billion computing hours per year to scientists (counting time on each core separately).
#6: Stampede, Texas Advanced Computing Center at University of Texas
With Dell PowerEdge servers powered by Xeon processors and an InfiniBand interconnect, Stampede scored 5.2 petaflops. It is one of the largest systems in the world devoted to open science research—any researcher at a US institution can submit a request to use some of its computing power.
#7: Juqueen, Jülich Supercomputing Centre in Germany.
Another Blue Gene/Q system, Juqueen’s 458,752 cores hit speeds of 5 petaflops. Using 2,301 kilowatts of power, Juqueen was rated the fifth most energy efficient Top 500 supercomputer last November.
#8: Vulcan, Lawrence Livermore National Laboratory
This 4.3 petaflop system is based on IBM’s Blue Gene/Q supercomputing technology and has 393,216 cores. This supercomputer isn’t devoted solely to government use; Vulcan was recently opened to industry and research universities for collaborative projects.
#9: SuperMUC, Leibniz Supercomputing Centre in Germany
Using IBM iDataPlex servers, 300TB of RAM, and an InfiniBand interconnect, SuperMUC’s 147,456 cores achieved a speed of 2.9 petaflops. Energy costs are cut by directly cooling chips and memory with water at unusually high temperatures of 104 degrees fahrenheit.
#10: Tianhe-1A, National Supercomputing Center in China
Ranked #1 in November 2010, Tianhe-1A uses Intel Xeon CPUs and Nvidia GPUs across its 183,368 processing cores for a rating of 2.6 petaflops.
 source: http://arstechnica.com/information-technology/2013/06/the-ten-fastest-supercomputers-on-the-planet-in-pictures/#image-1
source: http://arstechnica.com/information-technology/2013/06/the-ten-fastest-supercomputers-on-the-planet-in-pictures/#image-1
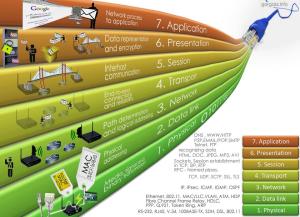
OSI Model
[This article use Indonesian]
OSI (Open System Interconnection) merupakan sebuah pemodelan yang digunakan untuk menjelaskan cara kerja komputer secara logika. OSI model mempunyai 7 layer yaitu Physical, Data Link, Network, Transport, Session, Presentation, dan Application. Masing-masing layer mempunyai fungsi dan perangkat yang berbeda di dalam suatu jaringan.
- Layer 1 – Physical Layer
Berfungsi untuk mendefinisikan media transmisi jaringan, metode pensinyalan, sinkronisasi bit, arsitektur jaringan (seperti halnya Ethernet atau Token Ring), topologi jaringan dan pengabelan. Selain itu, level ini juga mendefinisikan bagaimana Network Interface Card (NIC) dapat berinteraksi dengan media kabel atau radio.
- Layer 2 – Data Link Layer
Berfungsi untuk menentukan bagaimana bit-bit data dikelompokkan menjadi format yang disebut sebagai frame. Selain itu, pada level ini terjadi koreksi kesalahan, flow control, pengalamatan perangkat keras (seperti halnya Media Access Control Address (MAC Address)), dan menetukan bagaimana perangkat-perangkat jaringan seperti hub, bridge,repeater, dan switch layer 2 beroperasi. Pada layer Data Link terdapat 2 sublayer, yaitu lapisan Logical Link Control (LLC) dan lapisan Media Access Control (MAC).
- Layer 3 – Network Layer
Berfungsi untuk mendefinisikan alamat-alamat IP, membuat header untuk paket-paket, dan kemudian melakukan routing melalui internetworking dengan menggunakan router dan switch layer-3.
- Layer 4 – Transport Layer
Berfungsi untuk memecah data ke dalam paket-paket data serta memberikan nomor urut ke paket-paket tersebut sehingga dapat disusun kembali pada sisi tujuan setelah diterima. Selain itu, pada level ini juga membuat sebuah tanda bahwa paket diterima dengan sukses (acknowledgement), dan mentransmisikan ulang terhadp paket-paket yang hilang di tengah jalan.
- Layer 5 – Session Layer
Berfungsi untuk mendefinisikan bagaimana koneksi dapat dibuat, dipelihara, atau dihancurkan. Selain itu, di level ini juga dilakukan resolusi nama.
- Layer 6 – Presentation Layer
Berfungsi untuk mentranslasikan data yang hendak ditransmisikan oleh aplikasi ke dalam format yang dapat ditransmisikan melalui jaringan. Protokol yang berada dalam level ini adalah perangkat lunak redirektor (redirector software), seperti layanan Workstation (dalam Windows NT) dan juga Network shell (semacam Virtual Network Computing (VNC) atau Remote Desktop Protocol (RDP)).
- Layer 7 – Application Layer
Berfungsi sebagai antarmuka dengan aplikasi dengan fungsionalitas jaringan, mengatur bagaimana aplikasi dapat mengakses jaringan, dan kemudian membuat pesan-pesan kesalahan. Protokol yang berada dalam lapisan ini adalah HTTP, FTP, SMTP, dan NFS.